Learn how businesses like yours use Textmagic
Here is how the Textmagic business texting platform is helping businesses daily to grow their revenue and improve their productivity.
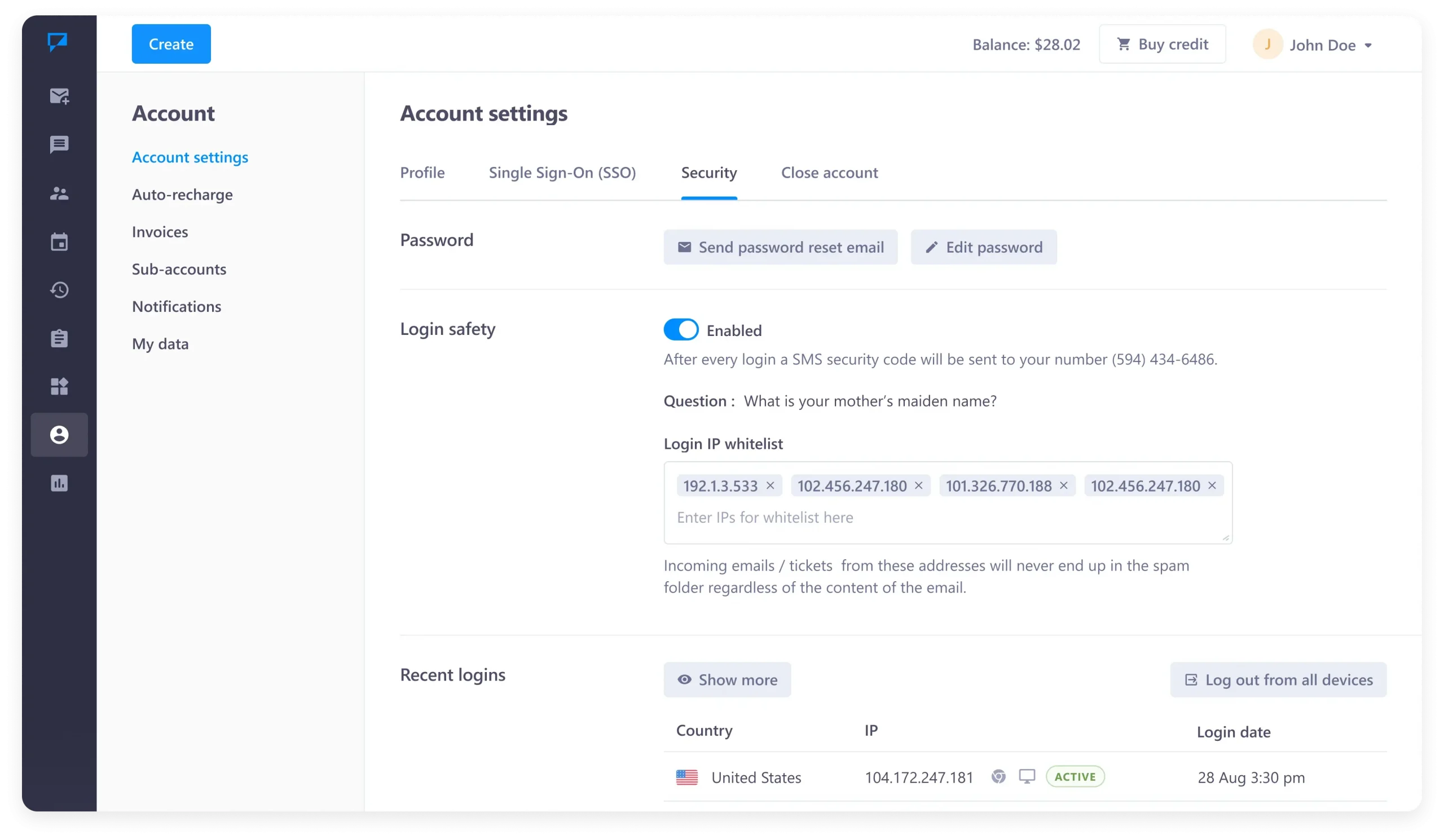
How Textmagic safeguards your online security
Security is a top priority for Textmagic. We have taken steps to safeguard the security of text messages sent through our SMS gateway, as well as online payments and actions that you conduct through our web platform.

Soc 2 Type II Certification
Textmagic is SOC 2 Type II certified. This confirms that our information security practices, policies, procedures, and operations meet
the highest security standard.
Our Information Security Program is also communicated throughout the organization with the help of Secureframe.

GDPR
We value our customers and their privacy rights. Since 2017, Textmagic has dedicated considerable resources to fully comply with the EU data protection requirements set forth by the General Data Protection Regulation ("GDPR"). Please read our dedicated GDPR page for more info about our security and compliance roadmap.
Organizational security
Third-party penetration testing
We perform regular external security penetration tests at least annually using certified vendors. The tests involve high-level server penetration tests and in-depth testing for vulnerabilities inside the application. All identified vulnerabilities are analyzed and remediated appropriately.
Soc 2 Type II certification
Textmagic is SOC 2 Type II certified. This confirms that our information security practices, policies, procedures, and operations meet the highest security standard. Our Information Security Program is also communicated throughout the organization with the help of Secureframe.
Security awareness training
Our team members are required to go through employee security awareness training covering industry-standard practices and information security topics such as social engineering, phishing scams, and hackers.
Roles and responsibilities
Roles and responsibilities related to our Information Security Program and the protection of our customer’s data is well defined and documented. Our team members are required to review and accept all of the security policies.
Confidentiality
All team members are required to sign and adhere to an industry-standard confidentiality agreement prior to their first day of work.
Third-party audits
Our organization undergoes independent third-party assessments to test our security and compliance controls.
Background checks
We perform background checks on all new team members in accordance with local laws.
Infrastructure security
Data hosting security
All our production data is hosted on OVHCloud bare metal servers. All these databases are located in France. Online database backup is hosted on Google Cloud Platform, located in the United States. Offline database backups are hosted on Amazon Web Services, located in the United States, and are subject to our data retention policy.
Encryption in transit
Our application uses industry-standard Transport Layer Security (TLS) to create a secure connection. This includes all data sent between the web, desktop, iOS, and Android apps and the Textmagic servers. There is no possibility to connect to Textmagic without TLS. The minimum supported version of TLS is 1.2. All connections are made securely over HTTPS.
Business continuity and disaster recovery
We use our data hosting provider’s backup services to reduce any risk of data loss in the event of a hardware failure. We utilize monitoring services to alert the team in the event of any failures affecting users.
Application infrastructure security
All of our services are hosted with OVHCloud, the largest hosting provider in Europe. They employ a robust security program with multiple certifications. For more information on our provider’s security processes, please visit OVHCloud Security.
Vulnerability scanning
We perform vulnerability scanning monthly and actively monitor for threats to ensure secure usage of our services.
Encryption at rest
All databases are encrypted at rest to protect the data of our customers from unauthorized access.
DDoS prevention
All requests to our infrastructure are routed through Cloudflare’s CDN network, which is built to withstand complex and large DDoS attacks.
Incident response
We have a process for handling information security events which includes escalation procedures, rapid mitigation, and communication.
Logging and monitoring
We actively monitor and log various cloud services.
Access security
Permissions and authentication
Access to cloud infrastructure and other sensitive tools is limited to authorized employees who require it for their role. Where available we have Single Sign-on (SSO), 2-factor authentication (2FA).
Least privilege access control
We follow the principle of least privilege with respect to identity and access management. This means that employees are only granted access to production infrastructure or tooling if their job role requires it. The whole access to production infrastructure or customer data is monitored.
Password requirements
All team members are required to adhere to a minimum set of password requirements and complexity for access.
Password managers
All company-issued laptops utilize a password manager for team members to manage passwords and maintain password complexity.
Quarterly access reviews
We perform quarterly access reviews of all team members with access to sensitive systems.
Vendor and risk management
Annual risk assessments
We undergo at least annual risk assessments to identify, analyze and mitigate any potential threats, including considerations for fraud. Once a risk is identified, Textmagic makes all possible steps to remediate any threats to protect our application system and customer data.
Vendor and risk management
Our service providers undergo a thorough security assessment as a part of the evaluation process and then go through regular SOC1, SOC2, and/or ISO/IEC 27001 audits thereafter. In the event, these audits have material findings, which present risks to Textmagic or our customers, we work closely with the vendor to track their remediation efforts until the issue has been resolved.