At one point or another, you might have gotten one of those SMS messages that look like promotions. But then, they pop up without your consent, and they require you to click a link or contact a third party.
While these messages might seem innocuous, promising discounts, rewards, or urgent attention to an account issue, they could very well be a smishing attempt in disguise. Smishing exploits the immediacy and personal nature of text messaging to catch individuals off guard, coaxing them into divulging sensitive information such as passwords, bank account details, and credit card numbers.
In this article, we delve deep into the mechanics of smishing, shedding light on real-world instances, examining its far-reaching consequences for individuals and organizations, and providing essential guidance on protective strategies. Let’s begin!
What is smishing?
Smishing, or SMS phishing, is a cybercriminal activity that combines SMS (Short Message Service) with phishing to deceive individuals into divulging sensitive information, such as login credentials, financial data, or personal identification information. This technique typically involves the perpetrator sending a seemingly legitimate and urgent SMS message, often containing links or phone numbers, to prompt the recipient to act immediately.
The message may impersonate reputable entities like banks, government agencies, or service providers to gain the trust of the targeted individual. The ultimate aim of smishing is to exploit the acquired information for fraudulent activities, such as unauthorized access, financial theft, or identity theft.
While smishing is similar to email phishing, they’re completely different. For one thing, malicious actors, or in this case, smishers, send fake messages through SMS rather than email.
Since 60% of consumers read messages, including scam texts, within 5 minutes of receiving them, this poses a major safety threat. To this effect, there is an urgent need to address SMS phishing and see it as the problem it is.
SMS phishing statistics
Smishing isn’t just a threat to individuals. In fact, it is also a critical threat in the business SMS marketing space. CBS records that US consumers lost about $330 million last year to scam texts.
But that’s not all. Proofpoint’s State of the Phish report for 2023 found that:
- One out of three people tried clicking a link or carrying out a risky action when faced with a phishing attack
- In 2022, 30 million phishing messages sent involved Microsoft services
- One out of three people don’t know what phishing or SMS phishing is
- Only 35% of companies conducted phishing simulations to raise more awareness about it
- One in 10 phishing threats ended up blocked due to user complaints
From these statistics, we can tell that not many people in organizations have a firm knowledge of phishing. And as time passes, more individuals and companies are at risk due to these SMS message scams.
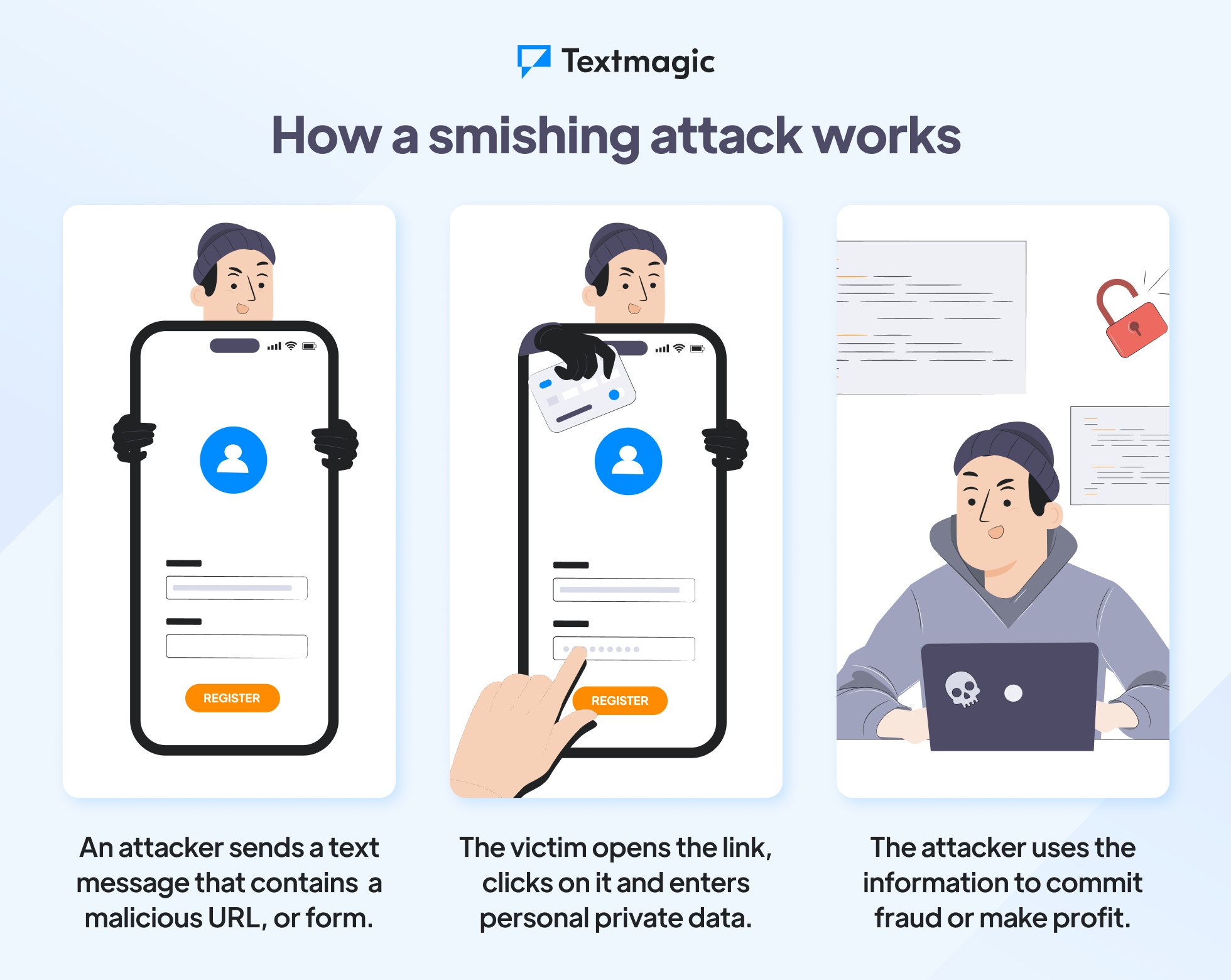
Common examples of smishing
Most smishing attempts involve casting a wide net by mass messaging numbers to phish for accounts most people have, such as bank accounts, Amazon accounts, and social media.
It is important to know the tell-tale signs of a text scam and look out for these common examples of SMS phishing:
Fake bank payments
This type of smishing attempt will pose as your bank informing you that someone has set up a new payment from your account. These play on your fear of a fraudulent payment to trick you into clicking the link or providing login details.
Account suspensions
These texts will falsely inform you that your account has been locked or suspended, often due to an unauthorized access attempt or failed payment. These texts will provide a malicious link asking for login details to recover your account.
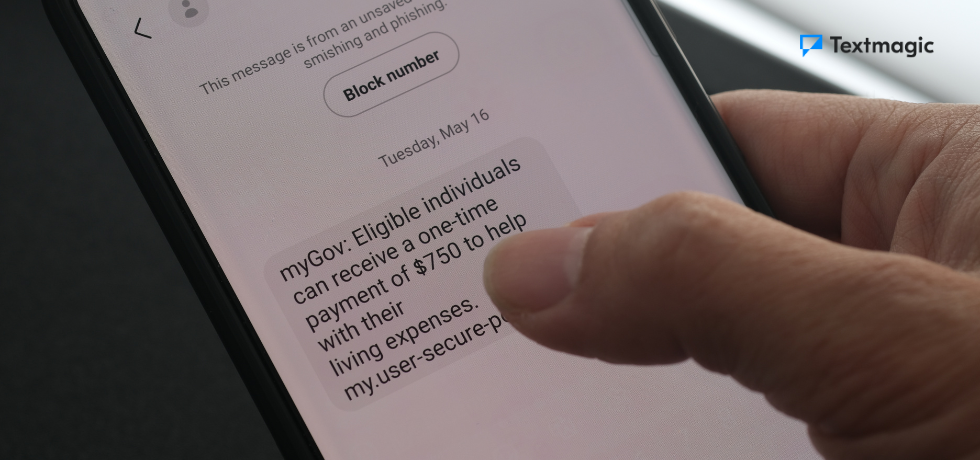
Government messages
Some smishing attempts will impersonate a government agency, often impose a fake fine, offer you a tax refund, or accuse you of tax fraud to provoke a response.
Fake competitions
You cannot win a competition you never entered. If you get a text saying you have won some competition you don’t remember signing up for, don’t reply. These texts will ask you for personal information in order to redeem a fake prize.
Social media impersonation
Various smishing SMS messages try to impersonate social media personalities. So, a text in this category could be someone pretending to be a popular artiste. They might even ask you to submit your details in a form to get fake financial benefits or send them funds for a fake project.
Urgent security alerts
These security alerts work by raising the alarm and feigning urgency that would push you to perform an action. For example, they could come as scam text messages alerting you of a false security threat.
Then, they’d request you to submit sensitive details via a form to protect yourself from a non-existent danger.
Emergency scams
Emergency scam messages are a little similar to urgent security alerts. However, the major difference is that the urgency in this case doesn’t stem from security. So you could receive a message requesting you to call them or reply when there’s actually no emergency.
Healthcare scams
Healthcare scams range from false emergency alerts about relatives’ health to offers for false healthcare plans. The SMS messages usually have a call to action that urges you to apply for a fake healthcare program or find out more about the relative’s well-being.

7 Tips to protect yourself from SMS phishing and fraud
SMS phishing may be getting more common, but there is a lot you can do to protect yourself. Following these seven rules will help you avoid becoming a victim of SMS phishing.
1. Don’t assume you’re safe
Letting your guard down makes you an ideal target for SMS phishing attempts. Most forms of SMS phishing are indiscriminate, mass messages sent to random numbers. Because of this alone, there is no reason to assume you will not receive one.
Furthermore, you may also be targeted more specifically as part of an attack on your business or businesses you work with. Most businesses work with a significant amount of customer data, making even small businesses valuable targets.
As a result, you need to be aware of SMS phishing tactics. Understanding how smishing works makes it much easier to spot.
2. Ensure sender validity
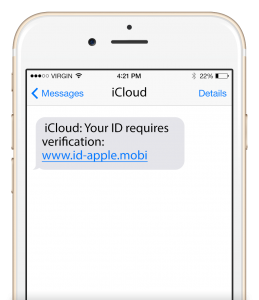
The most obvious way to spot a phishing attempt is to check if the sender is who they say they are. Some fraudsters use a fake shortcode to display the name of a legitimate bank or government organization, so a named shortcode is not a guarantee that the sender is real.
Instead, search the number online to find out who it belongs to. Confirming that the number belongs to a real business should be easy. If you are not 100% certain who a text is from, do not click any links or open any attachments in the message.
These links could take you to a site that takes your personal information or installs malware on your phone. If you get a suspicious text about an issue with your account or order, use the business’s website or app to check it out instead of following the link in their text.
3. Look out for bad spelling and grammar
To put it simply, legitimate businesses staff their customer service teams with people who can type correctly. If you receive a text full of spelling errors and poor grammar, this is often a sign of a phishing attempt. In many cases, it’s a deliberate action.
Obvious mistakes in a phishing message help fraudsters ensure they only get responses from the most unsuspecting targets.
4. Don’t give out personal information via text
Never give out any sensitive information via text. This includes your:
- Account usernames and passwords
- Bank details
- Credit card or other payment information
- Names and physical addresses
Legitimate businesses or institutions will never ask you to provide this kind of information via text.
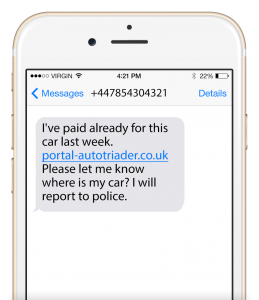
5. Never reply if you suspect fraud
Don’t reply to phishing attempts, even if they seem like an automated message with a STOP option. Criminals will not follow the regulations and stop texting when you send STOP.
This is included to make the text appear more convincing. A reply simply tells fraudsters that your number is actively used and can encourage further messages. It may also result in them sharing your number with other fraudsters as a known active line.
6. Don’t call the number back
Just as you should never reply to a text message scam, you shouldn’t call the sender back either. Sending a call to the phisher tells them that your line is active. And in the long run, you could become a target for messages and calls from other phishers.
On another note, calling the phisher exposes you to the risk of sharing sensitive information and our location with them. They might sound more convincing over the phone and might trick you into sending them money or giving them private details.
7. Report the SMS phisher immediately
Once you sense that you’re under a phishing attack, the best action is to report the phisher and block them.
In the United States, in 2010, the Global System for Mobile Communications (GSMA) designated “7726”, which spells out SCAM for reporting scam messages. And since most major carriers in the US are part of the GSMA, reporting scam messages to 7726 won’t carry extra charges. Additionally, you can file your complaints with the Federal Trade Commission at ReportFraud.ftc.gov
To report an SMS Phishing attack in the United Kingdom, simply forward the message to 60599. Remember that forwarding the message would cost you according to your local rates. And once you’ve done this, immediately block the number.
For iPhones, you can report any suspicious message by following the steps below:
- Open the spam message
- Touch and hold the message and click on “More”
- Click on the curved blue arrow on the screen, which means “Forward”
- Enter “7726” in the “To” field
- Press return to send it
For Android users, to report scam messages, follow the steps below:
- Open the message
- Click and hold it, then select “Forward”
- After your message appears as a new message, enter “7726 as the recipient’s number
- Select “Send”
After you’ve reported the message, your provider will send you a message on the next steps to follow.
Tools and resources
While trying to protect yourself from falling victim to SMS phishing attempts, you’re going to need some tools and resources. These help you avoid scam messages and keep fraudsters away from your information.
Here are three anti-phishing tools and resources you should know about:
Smartphone security apps
One of the effects of falling victim to SMS phishing could be introducing a virus into your phone. But, if you protect your device with smartphone security apps like anti-virus apps, password managers, and other anti-phishing software, that can help prevent the effects of phishing.
Smartphone security apps like Avast Mobile Security, Kaspersky, and Malwarebytes can protect you from such attacks. These apps secure your phone by detecting phishing attempts, safeguarding your passwords, and protecting private information.
Two-factor authentication (2FA)
Even if a phishing attempt is successful at acquiring your information, two-factor authentication can prevent fraudsters from using it. After setting up 2FA on an account, you will receive a unique code via text or an authenticator app for every login attempt.
Textmagic offers two-factor authentication services, which add an extra layer of security to user accounts and can help protect against unauthorized access, even if a user falls victim to a smishing attack.
Data from Google suggests that two-factor authentication can foil 96% of SMS phishing attempts. As a result, fraudsters will not be able to access your accounts without direct access to your mobile device or SMS inbox. Most text scammers are not hackers, and this is beyond their capabilities. In any case, threat actors are looking for the easiest targets, and doing this takes much more time and effort than spam phishing attempts.
Government and industry resources
Both the government and various industries have resources for reporting phishing attempts. For example, the Federal Trade Commission dedicated a section of its website to accepting and addressing phishing complaints.
In the United Kingdom, Gov.uk also has a section for phishing complaints. Alongside these government resources, companies like Microsoft have pages that help you protect yourself from phishing.
Conclusion
SMS scams are easy to spot when you know what to look for. Because of this, it is vital to stay aware of the latest tactics used by fraudsters and never assume you will not be a target.
Small businesses, in particular, are not only the most common target for smishing but often the least able to recover from the financial damage and loss of reputation. Make sure that everyone in your organization understands the potential threat of SMS phishing.
Furthermore, with the rising population of people and businesses falling into SMS phishing scams, there’s an urgent need for cybersecurity awareness. This knowledge would ultimately save both individuals and organizations and reduce the effects of these fraudulent practices.
Related articles
What is cloud telephony and how does it work?
The evolution of business communication has been mar...
What is a text blast and how to send one
When you need to get a message out quickly to a larg...
Texting in the UK: How to create a compliant SMS campaign
Text message marketing is completely legal in the UK...
How do scammers get your cellphone number and how to protect yourself
Scammers get your phone number and use highly sophis...
20 Business email examples to elevate your professional communication
Discover effective business email examples, template...