
Concepts such as SMS spoofing, smishing, and phishing have increased in popularity in the last few years. However, very few people know what sets the three apart or can offer clear definitions for each of these terms.
98% of cyberattacks are created using one or more elements of social engineering, like spoofing and smishing, but less than 35% of the population knows what smishing is. Let’s see what SMS spoofing is, how it works, and how you can protect yourself from it:
What is SMS spoofing?
To identify spoofing, you need to know exactly what it stands for and how it is used to steal sensitive information. We’ll be covering all that in a bit:
Definition of SMS spoofing
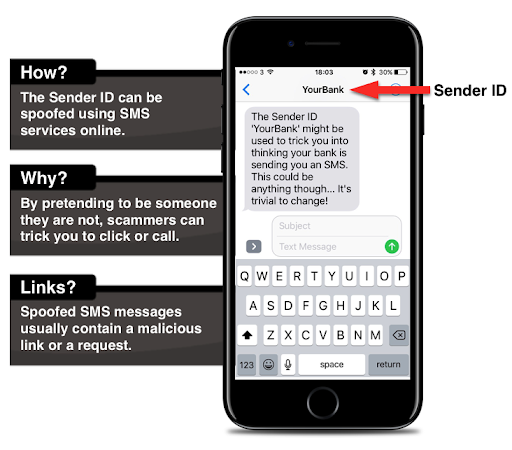
SMS spoofing is changing sender details like a phone number and/or contact name for fraudulent purposes. You cannot block a spoof text, or reply to it. The whole idea behind spoofing is impersonation.
You receive a text from someone you think you know, but in the end, things don’t add up. The name and/or mobile number are only similar to the ones people have in their contact list, but not the same.
Sometimes numbers are changed altogether. SMS spoofing is also known as “SMS originator spoofing” because it changes originator sender details.
Difference between spoofing and smishing
Spoofing and smishing are linked to phishing, a fraudulent attempt to get sensitive information for financial purposes. Smishing is also a fraudulent online activity, but it involves downloading a Trojan-type virus via SMS, which is how the relevant information is obtained from the user.
On the other hand, SMS spoofing only involves the alteration of sender details to make it look like the message is coming from someone they know and trust. Both, however, are scams.
How does SMS spoofing work?
SMS spoofing changes phone numbers and/or contact details to mislead mobile users. Victims receive a text that appears to be sent by someone they know. This type of cybercriminal activity involves falsifying data to obtain an illegitimate advantage.
The internet has been invaded with tools that alter names and mobile phone numbers. All it takes is one download, and fraudsters can send text messages from whatever number they choose, using names of well-known companies or even banks.
Some businesses even offer spoofing online services, but this borders on illegal. As long as the law remains uncertain, anyone can find their way around it and “help” scammers trick innocent users. Most such platforms offer their services at very low prices, which makes the scam even more attractive.
How fraudsters use spoofing to get sensitive user information
Fraudsters often change one letter, number, or symbol in the Sender details, to make their message seem valid. An example would be changing the letter L to an I to make it look like a company like PayPal is contacting you. Once you believe the message came from a trusted source, chances are you’ll click on the embedded link they sent and offer all the personal information they need.
Spoofing is not restricted to texts. It is also done via email, caller ID, or GPS receivers. The most common type of spoofing involves sending emails or texts to show a potential problem with a recent purchase you made or even a recent transaction.
Fraudsters don’t randomly target people; they target the ones who are waiting for delivery confirmations, bank transactions that are still pending, etc. They are more likely to click on links leading to malware or fake login pages simply because they are expected to take action. Identity theft, data breaches, and financial loss are only one click away.
Types of SMS Spoofing
1. Fake money transfers
Online shopping is one of the main areas where fraudsters operate. They visit online stores, add multiple items to their cart and then “attempt” to make the payment via bank transfer. If they have access to the number the store uses to get bank updates, the scam is complete. They then send a spoofed text message, impersonating the bank, which “confirms” that the transaction has been made.
Often, scammers will impersonate bank institutions and text victims about fake cash back transactions. This type of SMS smishing scam generally requests the user to scan a QR code or access the link to claim the cashback or complete another transaction.
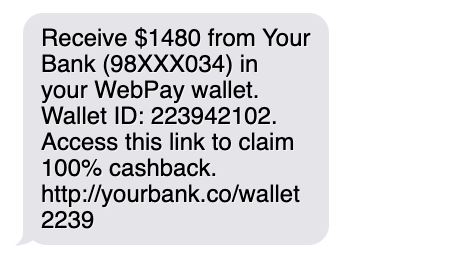
2. Fake sender IDs
Pretending to represent a well-known company can be highly productive, as it takes little to no effort. Let’s say you know someone’s house insurance will expire, and they will have to renew it.
Scammers can use this information to con people into renewing their insurance but redirect them to a site that has nothing to do with their insurance company. This is where phishing comes in: they add a link to their message, the user clicks on it, and the scam is complete.
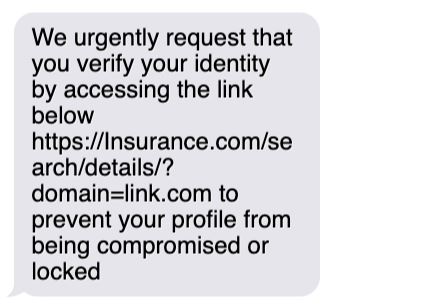
3. Harassment (stalking, pranking, family emergency, etc.)
SMS spoofing lets scammers assume any identity they wish. They don’t always use spoofing for financial reasons. Sometimes, it gets personal. Some use it to get back at people; others think it’s funny and start pranks, while some even use it to intimidate their victims long-term.
Scare tactics are very common among scammers, who often send texts telling families that someone close to them is in the hospital or has been arrested.

How to tell if a message is spoofed?
Spoof messages are pretty hard to differentiate from normal ones, but not for those who know where to look. It’s all in the details:
- The Sender Name field cannot be clicked and has a gray shade in spoofed texts, while in normal ones, you can click on it, and the color is blue;
- Spoofed messages often contain spelling errors and are not written in your native language;
- Since replying to spoof messages is not an option, scammers will ask you to contact them by phone or email. This is another sign that something is off;
- Common spoofing attempts include final notices, failed delivery notifications, account security breaches, pending invoices, and reset password requests;
- Refund scams are by far the most popular; users receive a text saying that they are owed a large sum of money because they were previously overcharged by a financial institution and have to provide financial information to receive the owed sum.
How to prevent SMS spoofing
- Never access SMS links. Always call the institution that requires this, in case anything looks suspicious. Banks never ask for sensitive details via SMS; they either require you to log in to their platform using your dedicated username and password or ask to see you personally at one of their offices;
- Carefully analyze sender details. Many spoofed messages contain grammatical errors or subtle changes in Sender Name and/or Number. Watch out for the small things before replying to any text message, especially if something seems off, like if the message contains an unusual request from someone you know or an institution you are in contact with;
- Never respond to imperative meszsages. Scammers usually want you to react on the spot because you might uncover their sham if you take your time. Whenever you receive a text that includes a sense of urgency, you should be suspicious;
- Always have a spam filter for your email address. This will redirect most spoofed messages to Spam;
- Never access sites with “No Lock” symbols or unencrypted URLs (HTTP instead of HTTPS) and always check to see the URL before clicking on it; you can do this by hovering over it or by holding your finger on the link for a few seconds if you are using a mobile device;
- Install a high-performance antivirus app for multi-layered protection on your phone and desktop.
Legal uses of SMS spoofing for business
Although SMS spoofing has a bad rep, it can be used for legal purposes as well. These include bulk SMS messaging, official messages, and instances where it is paramount to protect someone’s identity. Let’s go through all of these cases:
- Send bulk SMS campaigns. Companies connect with their target audience to promote their products or keep clients updated with upcoming events using mass text messaging.
Clients can send bulk SMS to staff, customers, and prospects at scale with the click of a button. The SMS sender ID feature offers complete control over how a company communicates with its clients. The company’s name is featured instead of a random phone number the clients won’t know, which increases open rates for marketing campaigns and is 100% secure against possible hacking attempts.
- Broadcast official messages. Another legal use of SMS spoofing involves official messages. Banks and prominent service providers spoof their messages to inspire trust. However, this can often backfire, as hackers can use famous financial institution names to request sensitive information from unsuspecting users. So it is best to double-check with your bank before sending out any information of the sort and never access embedded links from SMS messages.
- Preserve anonymity. Some people would rather remain anonymous when sending out text messages. They use spoof texts to send anonymous tips to the Police or other institutions while their identity remains protected.
Conclusion
Spoofing is a standard practice among scammers, but it is easily detected if you know where to look. If you are a victim of an SMS spoofing attack, it is best to contact law enforcement immediately.
You can report spoofing attempts by sending a SPAM message at 7726 if you are a US resident or accessing the fraud text reporting service.
Remember to keep your bank account and financial information safe by not replying to anonymous texts or even texts that seem acceptable at first glance.
Related articles
SMS geofencing: What it is and how does it work
Geofencing is one of the latest technological advanc...
Texting your way to success: Conversational commerce SMS
In 2021, the global conversational commerce market w...
12+ Appointment confirmation and reminder text templates
Businesses can leverage SMS marketing for sending te...
15 Brilliant cold email templates guaranteed to get you more sales
Have you ever used cold email templates and received...
12 Proven strategies to improve your customer service in 2025
Good customer service is a critical differentiator t...




