
As cyber criminals become more innovative in their efforts to break down users’ defenses, businesses must become more active in maintaining their data integrity.
One of the most effective methods of enhancing online security is through two-factor authentication text messages. This adds an additional layer of security by requiring not only a password and username but also a text message sent to the user’s phone in most cases. The goal is to make two-factor identification as easy as possible for end-users while at the same time ensuring that it is difficult, if not impossible, for hackers to bypass it.
The widespread of SMS 2FA in online platforms proves its effectiveness in adding a critical security layer that is both accessible and difficult for unauthorized factors to bypass. This method leverages the widespread use of mobile phones, making it a convenient yet powerful tool in the fight against online fraud and data breaches.
What is SMS 2FA?
SMS 2FA, or SMS Two-Factor Authentication, is a security process in which users are required to provide two different authentication factors to verify themselves, the second being a numeric code sent via text message to the user’s mobile phone.
This adds an extra layer of security to ensure that people trying to gain access to an online account are really who they say they are.
2FA vs. SMS 2FA: What’s the difference?
Two-factor authentication (2FA) refers to any method of verifying a user’s identity using two different factors: something they know (like a password), something they have (like a smartphone), or something they are (like a fingerprint). 2FA enhances security by combining two independent credentials: what the user knows and what the user has or is.
SMS 2FA uses the SMS (Short Message Service) system to send a code to the user’s mobile phone, which the user must enter on the website or app to gain access. This code serves as the second factor, relying on the premise that while a hacker might obtain a password, it’s much harder for them to also have access to the user’s physical device in real time.
How does 2FA work?
2FA adds an extra layer to authentication protocols. It can come in many forms. Sometimes, it is biometric, requiring that a voice, fingerprint, retinal scan, or some other unique item be part of the mix.
These need extensive record-keeping and PII (personally identifiable information) storage, which can add significantly to overheads, as well as cause additional security concerns should that storage ever be compromised.
However, while such techniques are possible, they’re not practical in most cases. Instead, institutions such as banks issue unique identity cards to (for example) operate an automated teller machine (ATM). Such cards are useless without the PIN (personal identification number).
This security relies on having a specific item and combining it with a particular piece of knowledge. Bank cards can be lost when a wallet is stolen or misplaced, but the cards themselves are useless without the PIN.
Two-factor authentication augments the traditional ’username’ and ‘password’ paradigm.
How does SMS authentication work?
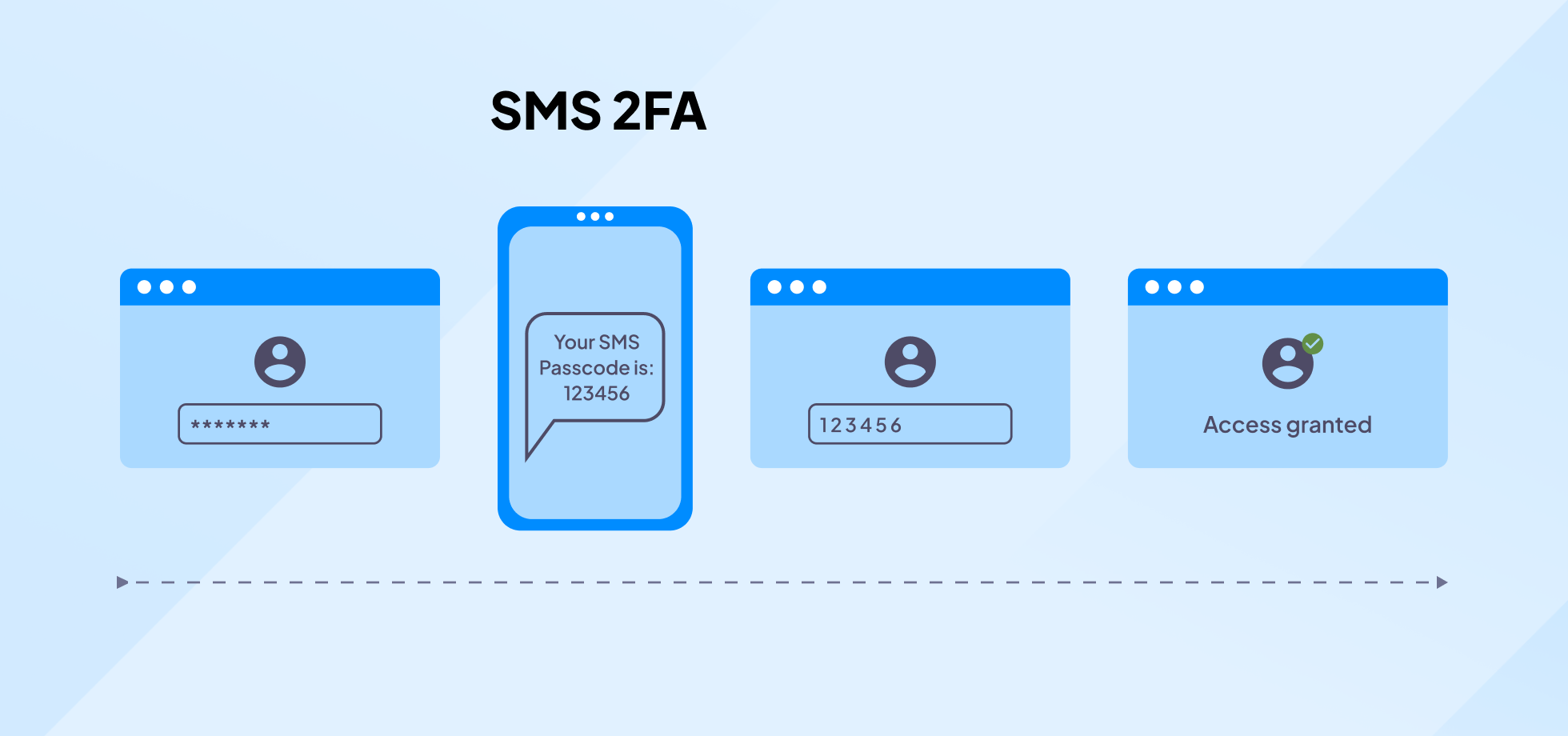
Text message two-factor authentication adds an extra layer of security to the login process, ensuring that only authorized users can access their accounts. Here’s a detailed breakdown of how this secure method unfolds:
Step 1: Enter username and password
Enter your username and password on the website or app you’re trying to access, just as you would with standard login procedures. The system verifies the credentials against its database to ensure they match an existing account.
Step 2: Request for text authentication
If the initial login is successful, the system triggers the second layer of security, text message authentication. The server sends a request to a mobile carrier to dispatch an SMS to the phone number associated with your account.
Step 3: Text message code generation
Wait for a text message to arrive on your mobile device. The SMS contains a unique, time-sensitive code, often consisting of numbers (and sometimes letters), generated by the system.
Step 4: Enter the code
After receiving the text, enter the provided code into the designated field on the website or app. The system verifies the code to ensure it matches the one it generated and sent.
Step 5: Authentication complete
If the code is correct and entered within the allowed timeframe, the system grants access to your account or transaction. If the code is incorrect or expired, you might be prompted to try again or go through recovery.
Pros and cons of SMS authentication
While SMS two-factor authentication enhances account security, it’s important to weigh its benefits against potential drawbacks. Here are the key pros and cons:
Pros of SMS 2FA
- Ease of use: Anyone with a mobile phone can receive text messages, making this method accessible and straightforward to use without the need for any additional hardware or software installations.
- Wide availability: SMS 2FA can be used with basic cell phones and does not require a smartphone or internet connection, expanding its applicability across various user demographics.
- No special apps required: Unlike app-based 2FA methods, SMS 2FA doesn’t require users to download or set up any specific applications, making it less effort-consuming for those who are less tech-savvy.
- Increased security: By adding an additional layer of security, SMS 2FA significantly reduces the chances of unauthorized account access compared to relying on passwords alone, as attackers would need to have both the password and access to the user’s mobile phone.
- Ease of implementation: Many service providers find SMS 2FA straightforward to integrate into their existing authentication frameworks, making it a quick win for improving user account security.
Cons of SMS 2FA
- Vulnerability to SIM swap scams: Attackers might trick mobile carriers into transferring a victim’s phone number to a SIM card in their possession. Once successful, they can receive the 2FA codes intended for the victim, potentially gaining unauthorized access to sensitive accounts.
- Phishing attacks: Users can be tricked into revealing their 2FA codes through phishing attacks. Attackers create fake login pages or send convincing messages, leading users to enter their codes into malicious websites.
- Interception risks: Text messages can be intercepted through various techniques, such as using a Stingray device (a type of IMSI catcher) or exploiting the Signaling System No. 7 (SS7) vulnerabilities in the cellular network, potentially exposing the 2FA codes to attackers.
- Social engineering attacks: Attackers can use social engineering tactics to convince mobile carrier employees to reroute a victim’s phone number to a new device or disclose sensitive information that could compromise 2FA security.
- Environmental factors: Users who lose access to their registered phone number, whether through losing their phone, switching numbers, or being unable to maintain service, can be locked out of their accounts until they can restore access to their text messages.

SMS 2FA alternatives
Exploring alternatives to SMS 2FA is important as organizations seek more secure and reliable methods to protect user data. Let’s examine some of these alternatives along with their advantages and disadvantages:
- Authenticator Apps: Apps like Google Authenticator and Authy generate time-based one-time passwords (TOTP) that change every 30 to 60 seconds, offering a more secure alternative to texts by eliminating the risks associated with message interception. These apps do not require an internet connection to generate codes, making them reliable and convenient for securing online accounts.
- Push notifications for approval: Services like Duo Security send a push notification to a user’s device for authentication. Users simply approve or deny access requests with a tap, providing a secure and user-friendly method that reduces the risk of unauthorized access through phishing or message interception.
- Universal 2nd factor (U2F) keys: Devices like YubiKey serve as physical tokens that a user can plug into their computer or connect via NFC to authenticate. U2F keys resist phishing and online attacks because access is granted only when the physical device is present, making them highly secure for sensitive applications.
- Biometric verification: This method uses unique physical characteristics such as fingerprint scans and facial recognition for authentication. Biometric verification offers a high level of security and convenience, as these characteristics are extremely difficult to replicate or steal compared to traditional passwords or codes, which is why biometric authentication is becoming an increasingly popular security technology in high-risk environments.
- Email-based 2FA: As an alternative to texts, some systems use email to send one-time codes or authentication links. While still vulnerable to phishing and account breaches, email-based 2FA can be more secure if combined with strong email account security measures, such as a unique, strong password and email encryption.
- Smart cards for physical authentication: Smart cards are physical tokens embedded with a chip that users must present for access to systems or facilities. They can store certificates and encryption keys, offering a secure method of authentication that combines something the user has with something the user knows (a PIN).
- Voice biometrics for identity verification: Voice recognition technology analyzes an individual’s voice patterns for authentication. This method provides a secure and convenient way to verify identity, leveraging the unique aspects of a person’s voice as a biometric marker that is difficult to mimic or steal.
- Behavioral biometrics analyzing user behavior patterns: This advanced method analyzes patterns in user behavior, such as typing rhythm, mouse movements, and navigation patterns. Behavioral biometrics offer continuous authentication that can detect anomalies indicative of unauthorized access, enhancing security by monitoring for consistent behavior patterns.
SMS 2FA vs. other 2FA methods
When comparing SMS 2FA to other 2FA methods, it’s important to understand the nuances and effectiveness of each approach in safeguarding digital accounts. Each method has its unique strengths and weaknesses, catering to different security needs and user preferences.
For a more detailed comparison, please refer to the tables below to see how SMS 2FA stacks up against its alternatives, highlighting key differences and considerations.
Security
| Method | Description |
|---|---|
| SMS 2FA | Vulnerable to SIM swapping, phishing, interception |
| Authenticator Apps (TOTP) | Resistant to remote attacks, no transmission involved |
| Hardware Tokens (U2F) | Highly secure, immune to remote phishing attacks |
| Biometric Authentication | Highly secure, uses unique biological traits |
Convenience
| Feature/Method | Description |
|---|---|
| SMS 2FA | High, accessible via any SMS-capable device |
| Authenticator Apps (TOTP) | High, requires a smartphone app |
| Hardware Tokens (U2F) | Medium, requires carrying a physical token |
| Biometric Authentication | High, uses physical traits like fingerprint |
Costs
| Feature/Method | Description |
|---|---|
| SMS 2FA | Low, no additional hardware needed |
| Authenticator Apps (TOTP) | Low, free apps available |
| Hardware Tokens (U2F) | Higher, cost of physical tokens |
| Biometric Authentication | Varies, dependent on device capabilities |
Dependence
| Feature/Method | Description |
|---|---|
| SMS 2FA | Dependent on mobile network availability |
| Authenticator Apps (TOTP) | Dependent on app and smartphone |
| Hardware Tokens (U2F) | Dependent on physical token presence |
| Biometric Authentication | Dependent on device’s sensor quality |
User Experience
| Feature/Method | Description |
|---|---|
| SMS 2FA | Simple, familiar process |
| Authenticator Apps (TOTP) | Requires app setup but straightforward usage |
| Hardware Tokens (U2F) | Requires physical action but simple |
| Biometric Authentication | Very quick and intuitive |
Scalability
| Feature/Method | Description |
|---|---|
| SMS 2FA | Easily scalable across many users |
| Authenticator Apps (TOTP) | Scalable, though requires users to have smartphones |
| Hardware Tokens (U2F) | Less scalable due to physical token distribution |
| Biometric Authentication | Scalable with equipped devices |
Recovery
| Feature/Method | Description |
|---|---|
| SMS 2FA | Potential risk if phone is lost or SIM swapped |
| Authenticator Apps (TOTP) | Recovery codes or backup options needed |
| Hardware Tokens (U2F) | Loss of token requires replacement |
| Biometric Authentication | May have issues if sensor fails or is damaged |
Conclusion
SMS 2FA stands as an essential layer of security, striking a balance between accessibility and protection. While it may not be the most impenetrable form of two-factor authentication, its ease of use and widespread applicability make it an invaluable tool for businesses and individuals aiming to safeguard their data against unauthorized access.
By choosing to incorporate SMS 2FA, organizations can significantly reduce the risk of data breaches, ensuring that customer information remains secure. Protect yourselves and your clients, as we’ve done for Cloud Data Service, a web and software development agency that relies on SMS 2FA security to make sure its clients’ information remains private.
If you want a reliable, secure communication channel for your clients, connect with one of our Textmagic experts via our online contact form or register for a free trial so you can see how it works for yourself!
Frequently Asked Questions (FAQs)
A 2FA text message is a one-time passcode sent via SMS. It’s used as a second layer of security to confirm your identity when logging in to online accounts.
SMS authentication is convenient but has vulnerabilities. Since messages can be intercepted or redirected, it’s less secure than other forms of two-factor authentication, like authenticator apps.
Banks rely on SMS 2FA to safeguard their customers’ accounts. The SMS code provides an additional step to verify that it’s really the account holder making the request.
When 2FA is enabled, you increase your account’s security by requiring a second factor for login, such as a one-time code sent to your phone or email after entering your password.
Textmagic offers 2FA to access your account. In addition to your password, you can enable 2FA and a unique code will be sent to your mobile device.
Yes, 2FA can be compromised. SMS-based 2FA is particularly susceptible to attacks such as SIM swapping and phishing, which can lead to the theft of your authentication codes.
Related articles
15 Effective follow-up email templates guaranteed to help you close more deals
Follow-up emails enhance business relationships and ...
Top 12 must-know customer service trends for 2025
Customer service plays a key role in business succes...
What is call masking and how can it benefit your business?
Have you ever had to call your food delivery courier...
5 Easy Pipedrive SMS integrations with Textmagic and Zapier
Pipedrive is a CRM software for businesses of all si...
7 Text marketing trends and predictions for 2025
As we usher in 2025, we can’t help but notice how th...




